eBook
The Elements of an Effective Security Strategy

This eBook shares how developing and implementing a long-term security strategy can bring order to your security environment, help you make better informed decisions, and take a more measured and proactive approach that protects your organization and its data over time.
This eBook Covers:
- The five elements of an effective security strategy
- Suggested threat areas to design against
- Security challenges organizations face with current cloud security models
- Bridging the gaps in security terminology in cloud
- Firewall design in the cloud
- Taking the next steps to develop a long-term security strategy
Download the eBook
How to Get the Most Out of Your Microsoft Secure Score
Microsoft Secure Score is one of the most useful tools in your security arsenal. This infographic is intended to highlight key aspects of the Secure Score – and offer recommendations to help ensure you derive maximum benefit from it.
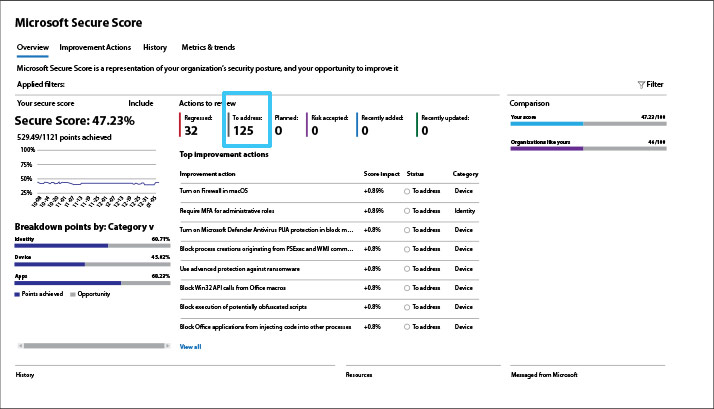
Understand your Secure Score
Your Secure Score is a snapshot of your current security posture as measured against a hypothetical perfect score of 100%. Your secure score should be looked at as a milestone in your progress toward a stronger security posture. The number isn’t as critical as maintaining an upward trend. What’s a “good” Secure Score? Of course, higher is always better – but it can vary, depending on your industry, environmental complexity, risk comfort level, and other business and technical factors. The important thing is to seek continuous improvement.
Recommendation: Review your Secure Score with a security services provider and develop an agreed-upon target score to aim for, along with an actionable plan to get you there.
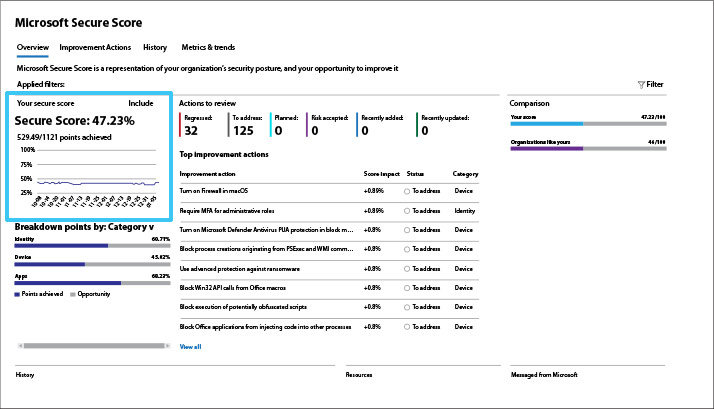
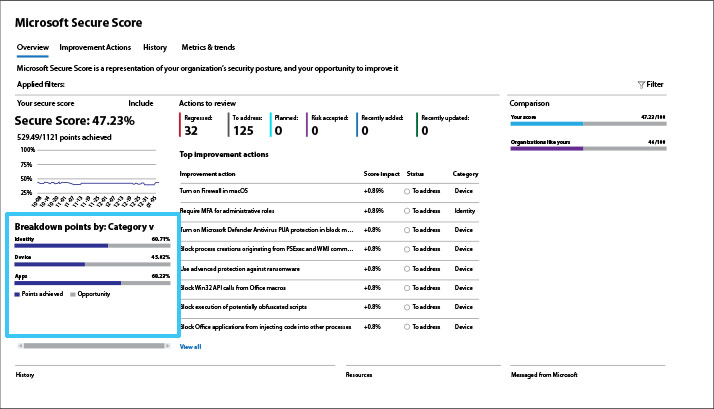
Pay attention to the category breakdown
The category breakdown provides clues to areas where you are most vulnerable – identity, devices, or applications. If one of these categories is out of sync with the other two, it could indicate a more pervasive problem that needs addressing.
Recommendation: Use the category breakdown to evaluate areas of concern and prioritize remediation actions. A significant improvement in a lagging category score can produce a major uptick in your overall score.
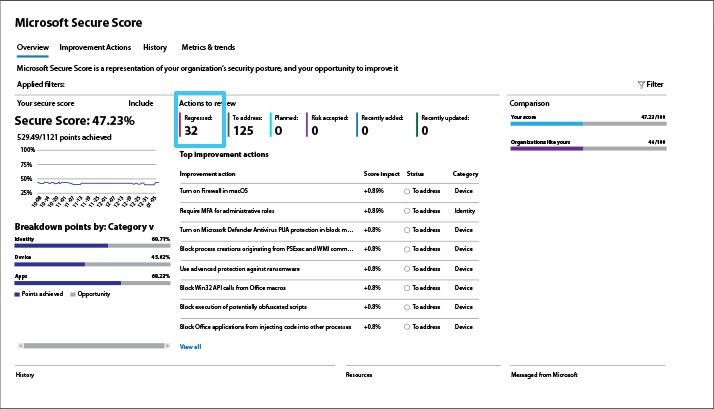
Mind your regression trends
What has lowered your Secure Score? Your regression actions number will tell you. The regression actions are likely due to user, configuration, or device changes.
Recommendation: Click on the “Metrics & trends” tab to see if regression is trending, and click on the “History” tab to view a timeline of activities and discover which actions have had a negative impact.
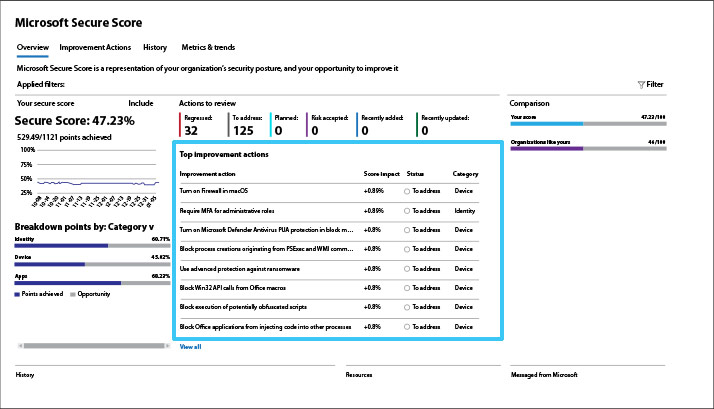
Get the greatest impact faster
Your Top Improvement Actions is a ranked list. The ranking is based on the number of points left to achieve, implementation difficulty, user impact, and complexity.
Recommendation: Tackle the highest-ranked improvement actions first and you will be assured of getting the greatest bang for the buck – and more quickly. Taking the top actions will be less difficult and complex while minimizing user impact and driving your overall score higher.
Think beyond your Top Improvement Actions
It’s important to remember that your Secure Score Top Improvement Actions only take into consideration your Microsoft products. Your IT environment likely includes many other systems and applications that are not covered in the Secure Score.
Recommendation: review your Secure Score with an IT security services provider that can build on its findings by considering other components in your environment and offering additional recommendations.
Recommendations Related to Security

Blog
7 Obstacles Keeping You from Improved IT Security
Everyone recognizes how essential security is, but few know how to move forward. We’ve identified the seven obstacles that frequently stand in the way.

Blog
How Your IT Service Model Affects Your Security Needs
There are many benefits of adopting a cloud-based IT service model. However, it’s important to understand the extent of security protection that your cloud provider manages versus your organization’s responsibility.

Checklist
Are You Secure?
This checklist is designed to help organizations stay aligned with cybersecurity best practices to create a robust IT security infrastructure to protect your network, data, applications, and devices.
Contact us
Questions?
Contact Melissa Carpenter (Smith)
Stay tuned
Connect with us and
stay in the loop
